Event ID 1121 – Exploit Guard – Microsoft Intune
Today I was getting Event ID 1121 in Windows Event Viewer while managing Windows Defender through Microsoft Intune. It took me a little bit of time to track down the exact cause as Microsoft have removed the GUIDs from the descriptions in the policy properties. I thought it would be a good idea to give an overview and include some useful references.
Background
Firstly, this blog applies to those running Attack Surface Reduction (ASR) through Microsoft Intune. These settings can be managed through Config Mgr or Group Policy but they are not in the scope of this post.
In this scenario, I have an ASR rule setup to point to a group of devices. The rule that I have setup, prevent Word from performing some legacy functions required in an old .Net 3rd party application. To fix the problem, the ASR rule needed to be changed.
Warning, make sure you have fully considered the consequences of lowering security rules in your organisation and always test before pushing live.
If you want to learn more about ASR rules, you can do some further reading from the Microsoft Docs Attack Surface Reduction Rules – Learn More | Microsoft Docs
The Problem – Event ID 1121
A third party application we use is producing this error in Event Viewer. The user is unable to use the application to retrieve the data they need.
This event information can be found here:
Event Viewer | Applications and Services Logs | Microsoft | Windows | Windows Defender | Operational
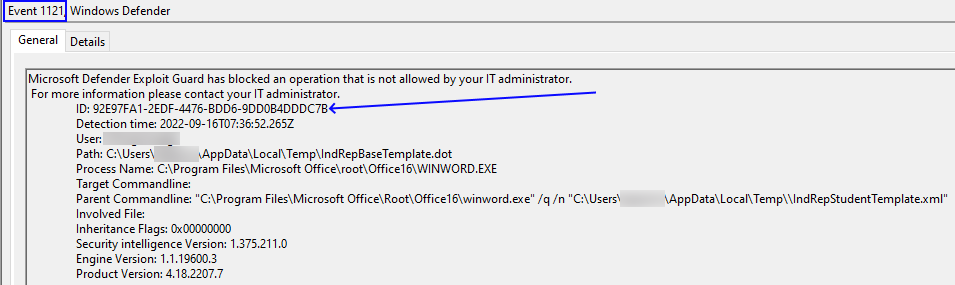
The details of the event show some very useful information. As you can see from the image below

If we unpack the details here, the key part is the ID which I have pointed directly at. This is what is going to tell you which part of the policy is affecting your users.
We can also confirm we have the correct error by checking the affected applications.
We can use this ID to work out the solution.
The Solution – Intune ASR Rules
Head over to Intune. Specifically in the Endpoint Security blade.
Endpoint Security | Attack Surface Reduction | Select your ASR rule for the affected device(s)
Select Properties and click Edit next to the Configuration Settings section
Now we need to use that ID from the event viewer details to determine the cause of the issue.
Unfortunately it looks like Microsoft have removed the GUID from the policy tip that used to appear next to each setting. So I have included a table below which should help navigate the policy easier.
In the GUID column you will find the ID from the Event Viewer entry details and in the Name you will find the name of the policy setting as it appears in Intune
| GUID | Name |
| e6db77e5-3df2-4cf1-b95a-636979351e5b | Block persistence through WMI event subscription |
| 9e6c4e1f-7d60-472f-ba1a-a39ef669e4b2 | Block credential stealing from the Windows local security authority subsystem (lsass.exe) |
| 7674ba52-37eb-4a4f-a9a1-f0f9a1619a2c | Block Adobe Reader from creating child processes |
| 75668C1F-73B5-4CF0-BB93-3ECF5CB7CC84 | Block Office applications from injecting code into other processes |
| 3B576869-A4EC-4529-8536-B80A7769E899 | Block Office applications from creating executable content |
| D4F940AB-401B-4EFC-AADC-AD5F3C50688A | Block all Office applications from creating child processes |
| 92E97FA1-2EDF-4476-BDD6-9DD0B4DDDC7B | Block Win32 API calls from Office macro |
| 26190899-1602-49e8-8b27-eb1d0a1ce869 | Block Office communication apps from creating child processes |
| 5BEB7EFE-FD9A-4556-801D-275E5FFC04CC | Block execution of potentially obfuscated scripts (js/vbs/ps) |
| D3E037E1-3EB8-44C8-A917-57927947596D | Block JavaScript or VBScript from launching downloaded executable content |
| d1e49aac-8f56-4280-b9ba-993a6d77406c | Block process creations originating from PSExec and WMI commands |
| b2b3f03d-6a65-4f7b-a9c7-1c7ef74a9ba4 | Block untrusted and unsigned processes that run from USB |
| 01443614-cd74-433a-b99e-2ecdc07bfc25e | Block executable files from running unless they meet a prevalence, age, or trusted list criteria |
| be9ba2d9-53ea-4cdc-84e5-9b1eeee46550 | Block executable content download from email and webmail clients |
| c1db55ab-c21a-4637-bb3f-a12568109d35 | Use advanced protection against ransomware |
To Fix
Once you have located the correct setting in the policy, you need to change it from Block to one of the other optional settings. You can change to
- Not Configured
- Block
- Audit Mode
- Warn [not available for all settings]
Warn is new and my favoured option here. This pops up a warning to the user that the action they are about to perform is risky. Gives them the chance to allow it. If they allow its, its only for 24 hours and then its automatically blocked again. The cycle will then repeat as many times as required.
After you have changed the setting, make sure you save the policy!
Remember
One thing you need to remember, once you have made a change in Intune, you need to sync your device settings.
You can hurry the process up by going to Settings | Accounts | Access Work or School | Click the connected Domain | Info | Sync
You may experience a delay for your settings to sync, I have seen this take 30 minutes plus, even with hitting the sync button.