Fine Grained Password Policy Setup – Active Directory
This post is all about how to setup Fine Grained Password Policy (FGPP) in On Premise Active Directory.
This may sound a little antiquated with the rapid uptake of Azure Active Directory (AAD) and all of its wonderful account security features, but lets not forget, for most organisations a hybrid model is the best they can achieve right now, so its important to make sure you are making the most of the security policies you have available.
What is Fine Grained Password Policy?
Fine Grained Password Policy or FGPP is nothing new. It’s been around since Server 2012 and put simply, it provides the ability to set password policies for users based on their group membership. It takes away the need for all of your users to have the same password policy. You can be targeted and specific to give those with the most privileged access the strongest password requirements and those with the least privileged access the less complex password requirements. This is excellent when you consider usability vs security.
For more information on FGPP, you can read through this Microsoft docs page Introduction to Active Directory Administrative Center Enhancements | Microsoft Docs
Prerequsites
What you need to get started…
- Windows server 2012 or above domain
- An agreed password policy for your organisation
Its worth reading through this article from the National Cyber Security Center (UK) on their password policy approach Password policy: updating your approach – NCSC.GOV.UK
Lets get started
First thing, you need to fire up the Active Directory Administrative Center – note, this is not Active Directory Users and Computers!
Once loaded, browse the Directory for the System container
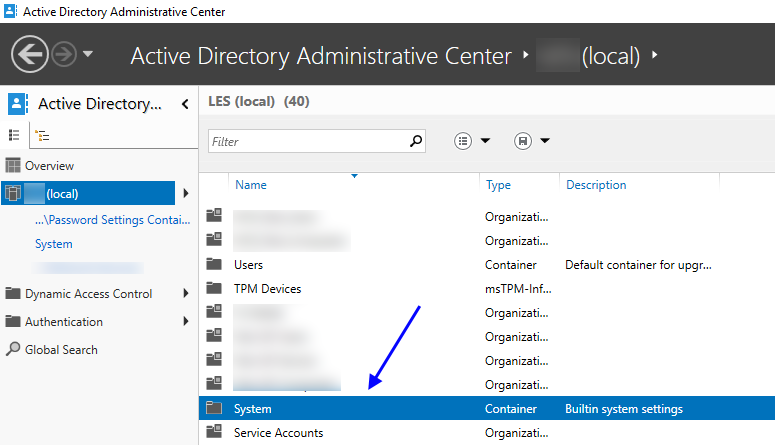
Open the system container and locate Password Settings Container
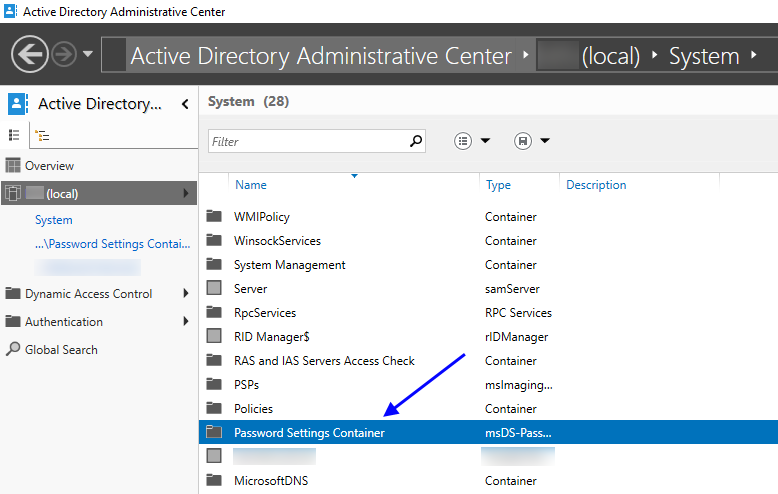
Open Password Settings Container and in any blank space, right click and choose New | Password Settings
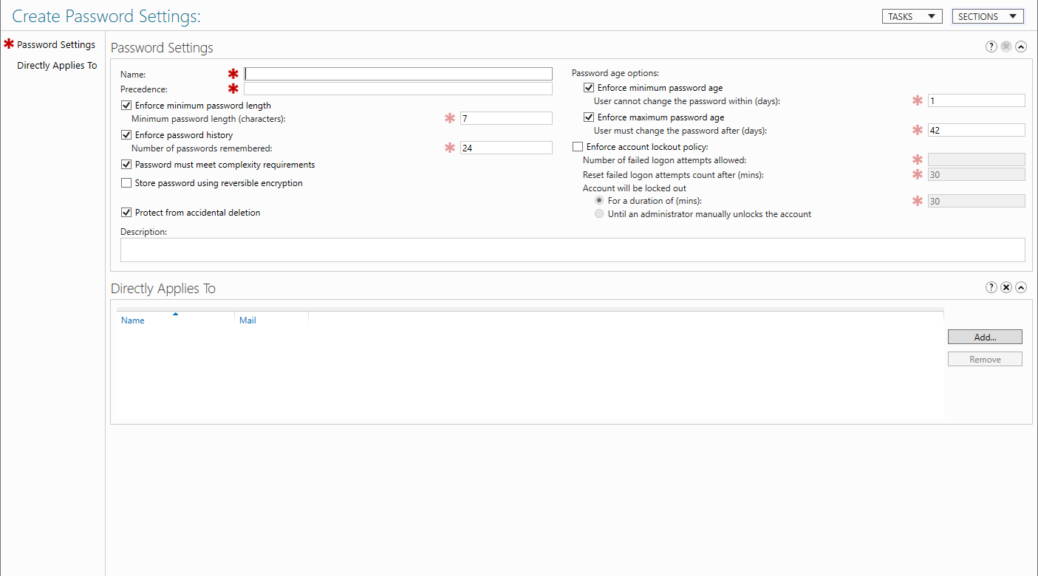
A window will open “Create Password Settings” Simply fill out the boxes below with the decided password policy for your organisation.
Red asterisk are fields that are mandatory.
Fields do not accept 0 as a value, in this instance you untick the box next to the setting, a tick implies its a setting that requires a value. If you wanted to remove the maximum password age for example you would not enter 0, you would untick the box next to the setting.
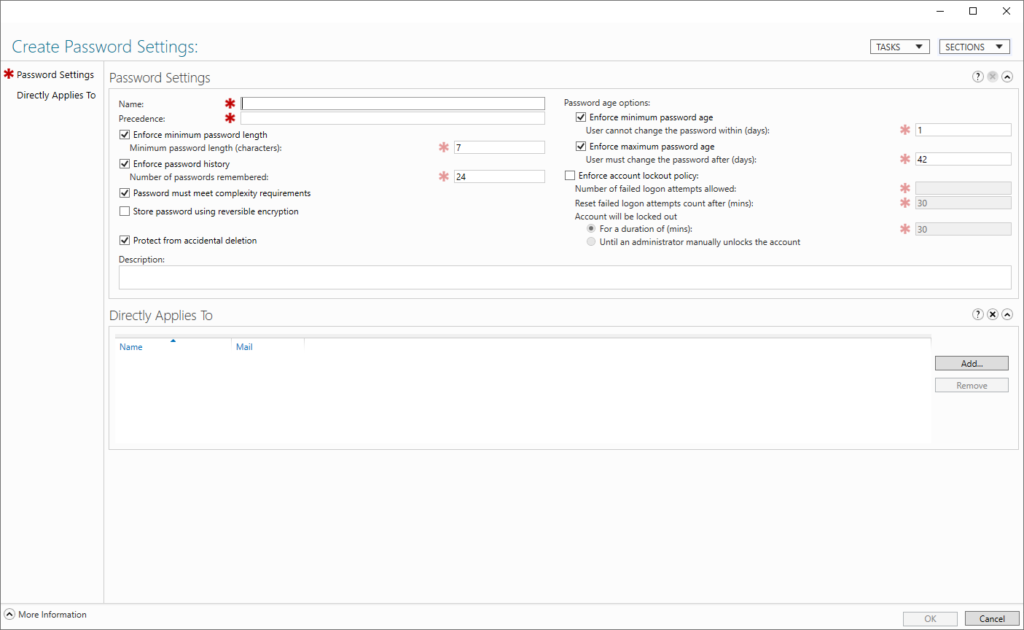
Its important to note the Precedence value is required.
You do not need to make this number unique but for ease of administration you should. This is how AD handles conflicts, if you have a user with two FGPP settings, the LOWEST precedence is applied to them.
If a user has two policies applied to them, both with the precedence as 2 for example then the policy with the LOWEST GUID is applied to their account. This is why its easier to try and keep the precedence value unique to each set of settings.
Tip: Start from 1 for your most secure accounts and build you polices upwards to 10 (or more) for your least privileged users.
Once you have populated your chosen password settings you need to Apply this policy to a user or group.
Note: Any groups you intend to apply this policy to must be either Security Group – Global or Security Group – Domain Local, you cannot use Security Group – Universal for this setup
The policies can be applied to either an individual or individuals or a group of user accounts.
Personally, I like to create a group per policy and add the users to it, that way I can easily identify who has what policy applied to them.
Save your new policy and its now active
Before you go – Some things to remember
Here are some things you need to know before you go and secure your user accounts.
Once the policy has been applied to your users, the changes to the password requirements DO NOT take effect until the user changes their password. So if you are trying to eradicate all four character passwords from your domain for example, then you need to enforce password resets on your users. You can of course so this by the policy you just setup using password expiry. Alternatively you could tick the boxes in AD for user must change password at next logon – though you need to make sure you clearly communicate this one!
Don’t forget about your Default Domain policy or any other Group Policies that you have password settings in. These polices will be overwritten by the FGPP policies so I would recommend you remove all password settings from all GPOs EXCEPT the default domain policy, keep that one setup as a medium strength password policy. Why? Because then you can ensure you have a safety net, a catch all, in case a group is not applied to a user.